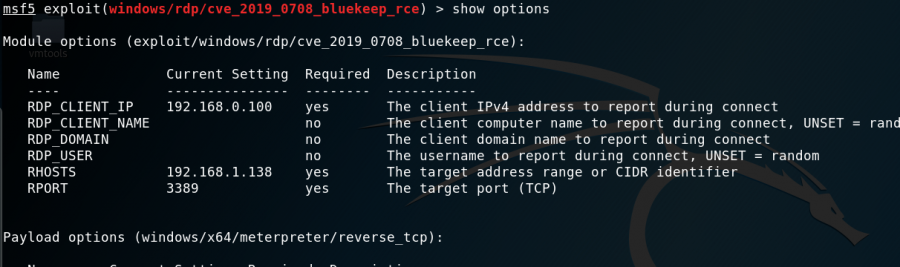
Over the summer, a security research team from Metasploit have been working on a proof of concept named ‘BlueKeep’. This exploit is based on the ‘WannaCry’ attack that a fellow Grey Hat hacker had used to target banks. This exploit targets the ‘Remote Desktop Protocol’ by Microsoft – enabling a hacker to gain entry to an older computer or server with Windows 7 or Windows Server 2008, and since then – may have advanced to target newer Windows systems. (refer to: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-0708)
There are a lot of articles floating around, pressuring tons of home & business users to “upgrade” their systems – stating that there’s about 700,000 machines, still vulnerable. However, we do not agree with the method they are proposing, here’s why…
1. Home users have their protocol hidden behind a home router, which by default – does not automatically port forward their RDP Port (3389) to a specific computer. Thus, this by itself – would prevent a hacker from being able to see or attempt to hack you with BlueKeep.
2. Professional IT Services, such as Supremacy and many others – deploy a network system which is able to examine packets automatically and to automatically ban bad actors based on rule-sets that they have deployed (as long as they know what they’re doing).
3. Metasploit, which is a package also installed on Kali (this is what Supremacy uses for penetration testing) – has allowed service providers to test their own systems against the hack, and allowed for us to create rules to prevent this, months prior to these warnings from the NSA & Microsoft.
4. Professional IT Services, no longer use the standard RDP for remote access to their client’s computers. Many of the service providers that we see, use services such as “Kaseya”, “LogMeIn”, “Bomgar”, “ConnectWise”, and many more. Supremacy uses ConnectWise – which is enterprise-grade software derived from Screen Connect.
5. Upgrading from Windows 7 to Windows 10 – there are a lot of compatibility issues with programs, even when ran under compatibility mode. This causes a lot of Windows 7 clients, to lose access to any older proprietary software that they developed/are currently using for their business. Also, the latest versions of Windows 10 – send a lot of information about your computer use to Microsoft and “Cortana” records everything you’ve search for… batches it up, and reports it back to Microsoft and the NSA for data gathering. This is proven.
So what is the real solution?
1. You can disable Remote Desktop Protocol, and use a secured remote control program.
2. There’s also the possibility of utilizing your network security, to automatically examine and deter bad actors. For home users, make sure that you are not port forwarding the RDP port (3389) to your computer’s LAN IP, by default – this port is NOT port forwarded.
3. Run nightly backups, make sure you have backups in 2 different locations. Make sure that the backup system, does not allow full access for the computer/server that you are backing up and only ‘Write’ access.
With these simple solutions, you’ll be able to withstand any ‘BlueKeep’ attacks if they ever come. And with the exploit further advancing – it wouldn’t surprise competent IT Admins, if the exploit began to cover newer systems such as Windows 8/10, or Windows Server 2012/2016/2019 in the future. For Microsoft, they are playing a game of catch-up. The ‘BlueKeep’ exploit was known about 1 yr ago (early 2018), within the hacking community. Info was released in late 2018, and Microsoft finally released a patch in early/mid 2019. With proper security implementation, most businesses were not affected.
If you would like to test it yourself, here are some free resources available as of 11/10/2019 @ 12:46PM.
1. Head to WhatIsMyIP.com (https://www.whatismyip.com/) and grab your WAN IP (simple terms; this is your IP Address for your internet service). Copy that IP Address (example: “Your Public IPv4 is: 108.108.108.108”)
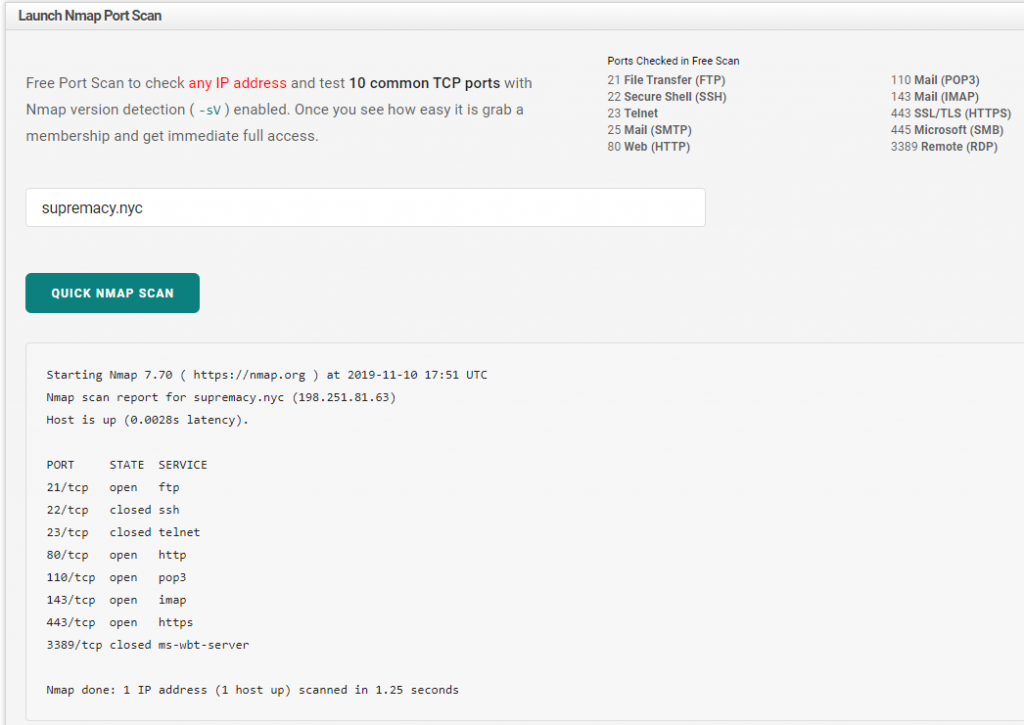
2. Then go to HackerTarget.com (https://hackertarget.com/nmap-online-port-scanner/) and use their NMAP scanner to scan your IP Address. This will show you what ports are opened and accessible to others. Look for port #3389. Below, I will provide an example – showing you the scan done against the ‘Supremacy.nyc’ server…
Lastly – we want to share this small piece of advice and insight… This exploit is nothing new. It was known and used by the NSA for over 5 years – before it was researched within HackForums.net and other hacking communities such as Rapid7 and DefCon. The NSA chose to use this exploit to their advantage, spying on vulnerable systems GLOBALLY… UNTIL it was publicly used by others. It would be wise not to rely on Microsoft patches… as they are usually slow, and after the fact. Take preemptive measures to secure your systems, do it diligently. Your data is important.